
SmashEx is an attack that exploits re-entrancy vulnerabilities in the exception handling designs of Intel SGX (Software Guard eXtensions) enclave runtimes. It is powerful enough to allow an attacker to read secrets or perform arbitrary code execution inside the victim enclave.
In response to SmashEx, both Intel and Microsoft have released security advisories for their enclave runtimes Intel SGX SDK and Microsoft Open Enclave. More related resources can be found here.
How Does It Work?
SGX is designed to protect user-level enclave code against a hostile or compromised OS software. For normal functioning, the SGX design allows the OS to interrupt the enclave execution through configurable harware exceptions at any point. This feature enables enclave runtimes (e.g., Intel SGX SDK and Microsoft Open Enclave) to support in-enclave exception or signal handling, but it also opens up enclaves to re-entrancy bugs. SmashEx is an attack which exploits enclave SDKs which do not carefully handle re-entrancy in their exceptional handling safely, which is complex on SGX. The SmashEx proof-of-concept exploits enable code reuse (e.g., ROP) and confidential data disclosure attacks in enclaves built with vulnerable enclave runtimes.
Demo Screenshots
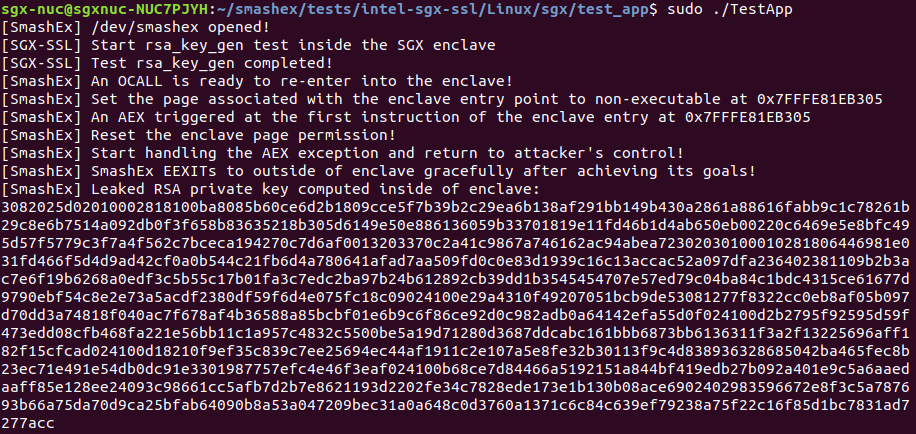
Leaking an in-enclave RSA private key from Intel SGX SSL
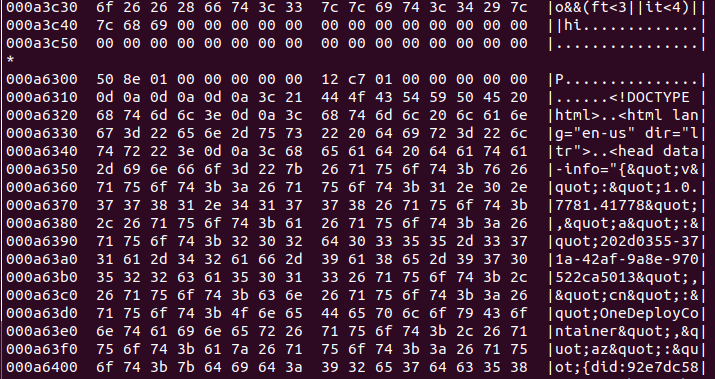
Dumping all enclave data from Open Enclave cURL
Root Cause Analysis
SmashEx arises due to the lack of atomicity primitives in SGX enclaves. Unlike an OS kernel or a traditional application which may request a trusted entity (the hardware or the OS in the examples) to block either the asynchronous occurrence or the asynchronous delivery of exceptions, software running inside an SGX enclave does not have easy access to such primitives since the OS is untrusted and the SGX hardware does not provide them. Without such primitives, an SGX enclave can be interrupted and re-entered at any time, including when it is in a state unsafe for re-entry (i.e., when it is executing a critical section). This gives the attacker opportunities to create and exploit such unsafe enclave re-entries.
Known Affected Runtimes
Older versions of the following runtimes are confirmed to be affected by SmashEx.
| Runtime | Vendor | Affected SGX generations |
|---|---|---|
| Intel SGX SDK | Intel | SGX2 |
| Open Enclave | Microsoft | SGX1 and SGX2 |
| Google Asylo | SGX2 | |
| EdgelessRT | Edgeless Systems | SGX1 and SGX2 |
| Rust SGX SDK | Apache | SGX2 |
| Teaclave | Apache | SGX2 |
| SGX-LKL | Imperial College London | SGX1 and SGX2 |
| CoSMIX | Technion | SGX2 |
| Veracruz | ARM | SGX2 |
FAQs
Intel Software Guard eXtensions (SGX) is a new form of hardware isolation technology to enable Trusted Execution Environment (TEE) on widely used Intel processors. SGX allows user applications to be partitioned into hardware-isolated compartments called enclaves, which are protected from privileged system software (e.g., hypervisor and the OS). The main guarantee provided by enclaves is protecting the confidentiality and integrity for code running in them.
If the runtime you are using is based on any of the runtimes listed above, you are almost certainly affected. Otherwise, please check with the developers of your runtime. You may help us maintain the affected runtime list by reporting to us.
Almost all of the versions before Intel SGX SDK v2.13 for Linux and v2.12 for Windows and Microsoft Open Enclave v0.15.0 are all vulnerable to SmashEx.
Follow the official advisories from your enclave runtime vendors if they are available. Otherwise, update the runtimes to the latest version.
Yes. SmashEx enables an attacker to reveal the victim enclave memory contents in full.
Yes. SmashEx enables an attacker to copy arbitrary code to the enclave memory and execute it.
Both Intel SGX SDK and Open Enclave have included patches to defend against SmashEx in their latest release versions. Their patches are purely software-based and trade the enclave functionality for security. As hinted at above, we believe that providing atomicity support in hardware is a better defense in the long run.
Yes. CVE-2021-33767 (Microsoft) and CVE-2021-0186 (Intel).
At the onset, SmashEx may seem conceptually close to known prior attacks on enclave memory safety (The Guard’s Dilemma), synchronization (AsyncShock), and scheduling (Game of Threads). However, they are in fact significantly different. SmashEx is the first attack that demonstrates the exception handling attack vector on Intel SGX. SmashEx does not assume any side channels or pre-existing memory safety bugs in the enclaved application code.
In contrast to attacks such as Iago and A Tale of Two Worlds which exploit the synchronous interface between an enclave and the untrusted OS, SmashEx exploits the asynchronous interface between them.
Unlike side-channel attacks on SGX enclaves such as Spectre and controlled-channel attacks, SmashEx can directly corrupt the enclave private data and break the enclave integrity.
Yes. The PoC exploits are available for research and education purposes only. You can find them here. Please contact us if you have problems obtaining the PoCs through the link above.
Because it Smashes SGX enclaves using Exceptions.
Please read our CCS 2021 paper or contact us.
Yes. The logo is free to use, with rights waived via CC0. It was designed by Valentina Caruso. Different formats are available: horizontal text, vertical text.
Authors
- Jinhua Cui (National University of Defense Technology)
- Jason Zhijingcheng Yu (National University of Singapore)
- Shweta Shinde (ETH Zurich)
- Prateek Saxena (National University of Singapore)
- Zhiping Cai (National University of Defense Technology)
Resources
- Security advisories: Intel, Microsoft
- Podcasts: Chips & Salsa (from Intel)
Citation
@inproceedings{smashex2021,
author = {Cui, Jinhua and Yu, Jason Zhijingcheng and Shinde, Shweta and Saxena, Prateek and Cai, Zhiping},
title = {SmashEx: Smashing SGX Enclaves Using Exceptions},
year = {2021},
doi = {10.1145/3460120.3484821},
booktitle = {Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security},
pages = {779–793},
keywords = {re-entrancy vulnerability, code-reuse attack, exception handling, tee, intel sgx, atomicity},
location = {Virtual Event, Republic of Korea},
series = {CCS '21}
}
Acknowledgments
We would like to thank Intel and Microsoft for working with us during the responsible disclosure.
This work was supported by Crystal Center at National University of Singapore. This material is in part based upon work supported by National Natural Science Foundation of China (62072465).